About
Our services around the CMDB i-doit
Consulting & Conception
beconadvises you on the licensing and requirement-oriented use of i-doit on the basis of best practices. In addition to the design of the architecture, all future integrations of third-party applications, data interfaces, individual add-on developments and special security requirements are taken into account in a concept.
Training & instruction
becontrain you even before the i-doit installation. In doing so, the requirements understood in the concept are taken into account and exemplified. Thus, it is clear to all sides what can be expected from an implementation. Supplemental admin and operator training can follow an implementation.
Installation & Customizing
becon performs a well-planned installation of i-doit for you incl. of all add-ons with focus on the add-ons Documents, VIVA and Analysis. In addition, becon takes over the customising – if required also according to complex criteria – as well as the implementation of application connections and security measures (encryption, anonymisation, data separation, secure data storage).
Integration & Development
beconintegrates i-doit into your IT process landscape. The APIs of ticketing, monitoring, configuration management, identity management and SIEM are used. Integration examples: JDisc, OTRS, Zammad, Remedy, openITCOCKPIT, Icinga2, Sensu, openNMS, Zabbix, SaltStack, Active Directory. In addition, i-doit data can be imported, exported and synchronized, and individual add-ons can be developed.
Support & operational support
beconsupports you flexibly from classic support according to different performance levels, to a spontaneously callable annual contingent with guaranteed response times, to employee leasing (ANÜ) for the support of your operation.
Industry know-how & solutions
beconoffers i-doit services across all industries. In the following industries becon has acquired specialist knowledge and developed specific best practices for i-doit: Information Technology, Telecommunications, Healthcare and Public Administration.
Advantages
The advantages of i-doit – The 360° IT documentation software
i-doit is more than just the best open source based platform for IT Documentation. With an intelligent relationship model, the ability to model IT services, manage configurations to devices and applications, and visualize dependencies and statistics, i-doit becomes a business-ready CMDB.
360° IT Documentation
Individual rights system
Free definition of relationship models
Extensibility through a multitude of add-ons
Immediate operational readiness without time-consuming introduction
More cost effective than other solutions on the market
Industry standard from practice for practice
Fair licensing model
premium partner
becon is i-doit Premium Partner,Certified Support Partner and Development Partner of synetics GmbH and thus provides the all-round carefree package.




premium partner
becon is i-doit Premium Partner,Certified Support Partner and Development Partner of synetics GmbH and thus provides the all-round carefree package.




premium partner
becon is i-doit Premium Partner,Certified Support Partner and Development Partner of synetics GmbH and thus provides the all-round carefree package.




Extensibility
becon add-ons from i-doit
The integration of i-doit pro add-ons opens up new possibilities for you to strengthen your system with additional functions, extended interfaces and enhanced evaluation options.
Extensibility
becon add-ons from i-doit
The integration of i-doit pro add-ons opens up new possibilities for you to strengthen your system with additional functions, extended interfaces and enhanced evaluation options.
One documentation for all use cases
Connect the departments of your company with each other.
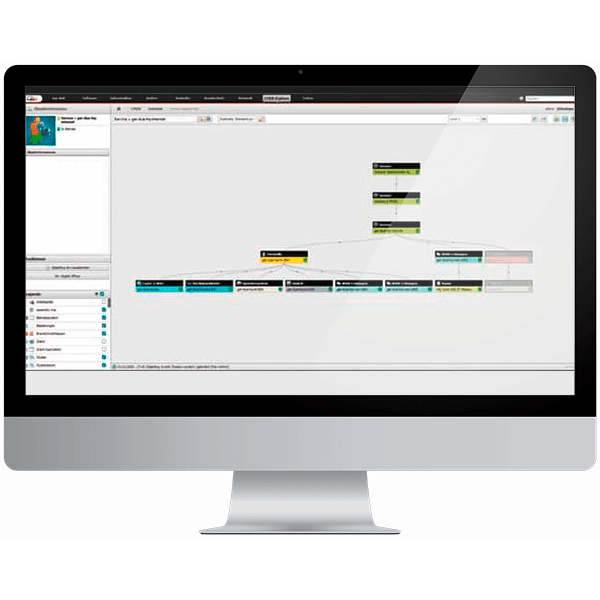
The start of your IT Service Management
You can connect countless other systems via many integrated interfaces.
One documentation for all use cases
Connect the departments of your company with each other.

The start of your IT Service Management
You can connect countless other systems via many integrated interfaces.

Request now!
How you benefit from systematic IT documentation with i-doit
With i-doit, IT managers gain an overview of their overview of their data center infrastructure, which greatly supports far-sighted and strategic IT management in times of increasing digitalization and brings quantifiable benefits:
You can see where hardware or license purchases can be bundled and negotiate better terms.
You can better plan updates and maintenance procedures because dependencies within your data center infrastructure become visible and show which infrastructure or company areas may be affected.
See how different IT services are really being used and optimize license management and maintenance contracts.
You gain a reliable basis for resilient risk analyses if you want or need to conduct systematic risk management for legal or business reasons.
About
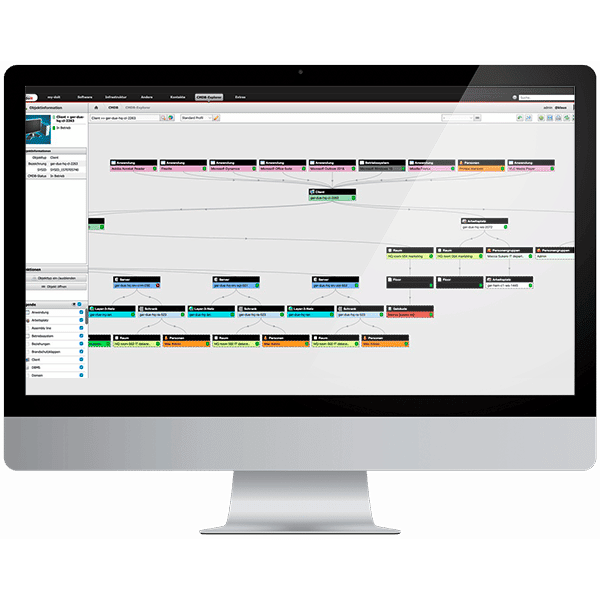
Data integration and interfaces
An open API and separate add-ons and extensions also make i-doit the control center of data center operations. Once all configuration items have been captured, they can be made available to all adjacent processes for further processing. This eliminates the need for manual maintenance of system data such as host name, IP, software, etc. in the Availability, Performance, Risk, Incident, Problem, Change and Release Management ITSM processes.
A big advantage of i-doit is not only the sharing of data, but also the many possibilities of data mining. Data can be imported via automatic scans from inventory and discovery or via the API.
About
Data integration and interfaces
An open API and separate add-ons and extensions also make i-doit the control center of data center operations. Once all configuration items have been captured, they can be made available to all adjacent processes for further processing. This eliminates the need for manual maintenance of system data such as host name, IP, software, etc. in the Availability, Performance, Risk, Incident, Problem, Change and Release Management ITSM processes.
A big advantage of i-doit is not only the sharing of data, but also the many possibilities of data mining. Data can be imported via automatic scans from inventory and discovery or via the API.
Couldn’t attend the i-doit Compliance Roundtable LIVE? No problem. We recorded the event for you.
Request recording from Compliance Roundtable
Couldn’t attend the i-doit Compliance Roundtable LIVE? No problem. We recorded the event for you.
Request recording from Compliance Roundtable
Service Management
Thei-doit Compliance Suite gathers all important tools for your IT security in one place: CMDB, ISMS, data protection and change management
OpenCelium –
The integration platform for i-doit
360° IT Documentation
i-doitProfessional – An ISMS with the advantages of a generic CMDB
Security
In addition to the introduction of i-doit, we also support you with our experience during the audit preparation.
becon blog
More articles on this topic
Contact
Instant contact
Do you have any questions, suggestions, requests or are you facing a particular challenge? We look forward to hearing from you!









